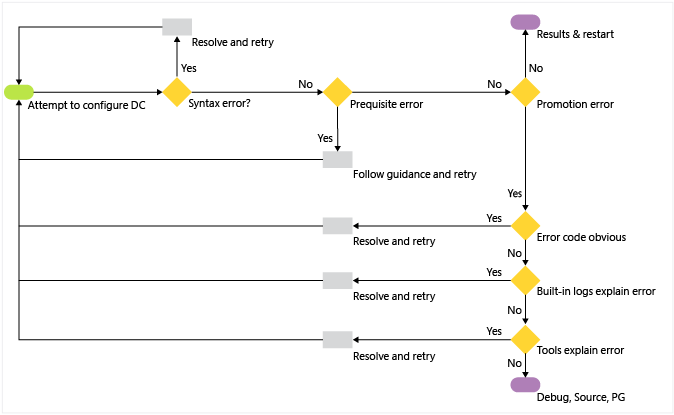
Domain Controller Dns Query Log
Dns analytical logs are not enabled by default and typically will only affect dns server performance at very high dns query rates.
Domain controller dns query log. Detail of threat log with suspicious dns query. I did not enable the client dns log as you described above. A pan os device s threat logs show suspicious dns query triggers. While win7 is on the way the out the client dns log on it does not capture the actual queries win10 does.
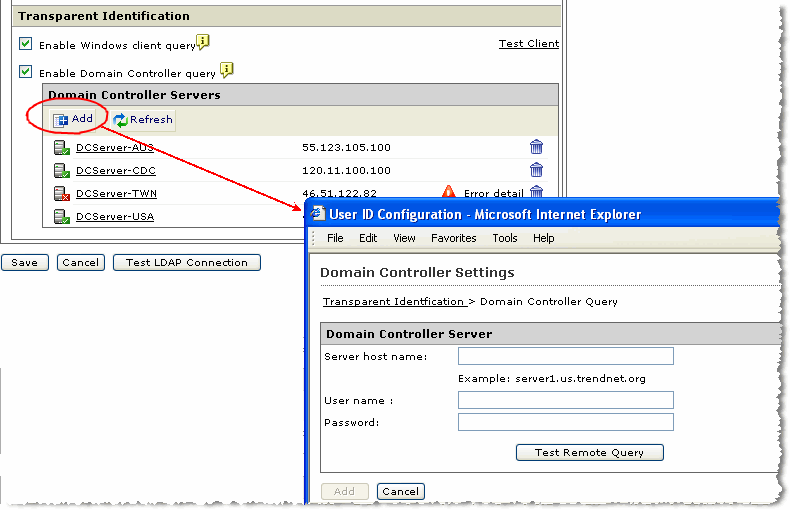
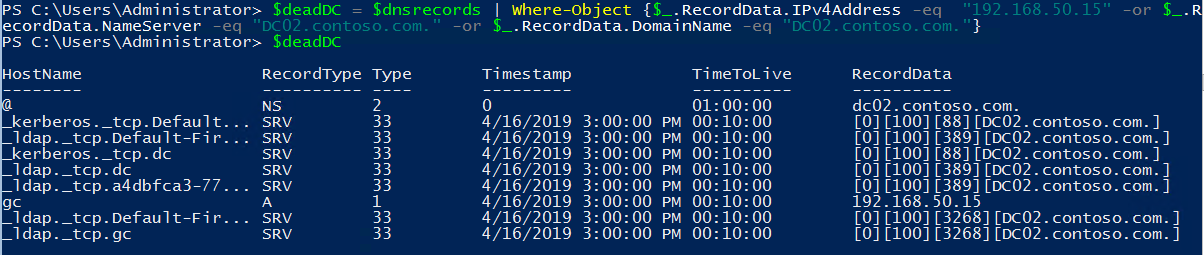
Is there a log for the domain controllers to query to determine which workstations are making dns requests and to where. They need a way to audit this to look for. Clients find their domain controller s and other important ad services by dns queries this means that your clients must use your domain controller s as their nameservers. Let s take a look at the key dns records and some other helpful information for troubleshooting dns issues.
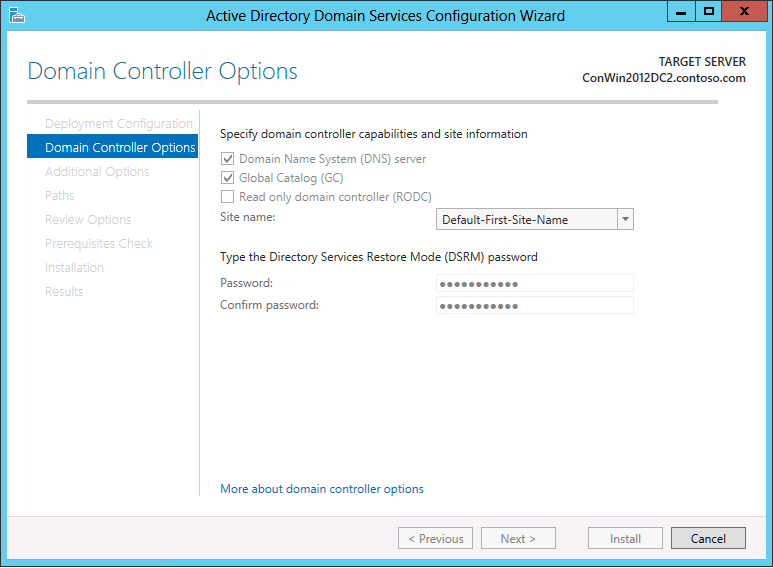
Nslookup is a command line tool that displays information you can use to diagnose domain name system dns infrastructure. The configuration wizard has automatically configured the dns settings according to the general recommendations from microsoft. Click ok and your done. Clients use dns records to discover and communicate with domain controllers which in turn allows for proper domain functionality.
By mitchell grande dns plays a central part in active directory. Doing it this way you only have to enable the collection of the sysmon logs for the collection using wec. Maybe something here helps. For example a dns server running on modern hardware that is receiving 100 000 queries per second qps can experience a performance degradation of 5 when analytic logs are enabled.
Administering dns on linux unix with samba tool creating a new zone. This powershell script connects to each domain controller specified in the dclist txt file and then collects the name of the event log to query the destination domain controllers from the querylogs txt file. It can be a secondary copy of the logs background. To collect the domain controller names from the active directory forest you can run dsquery server o rdn c temp dclist txt command.
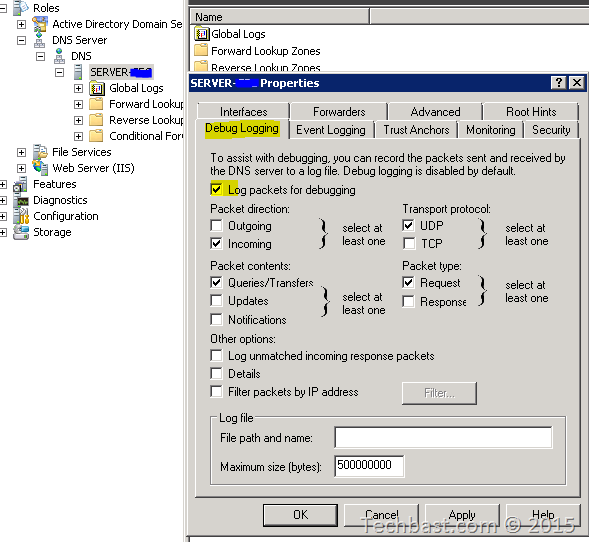
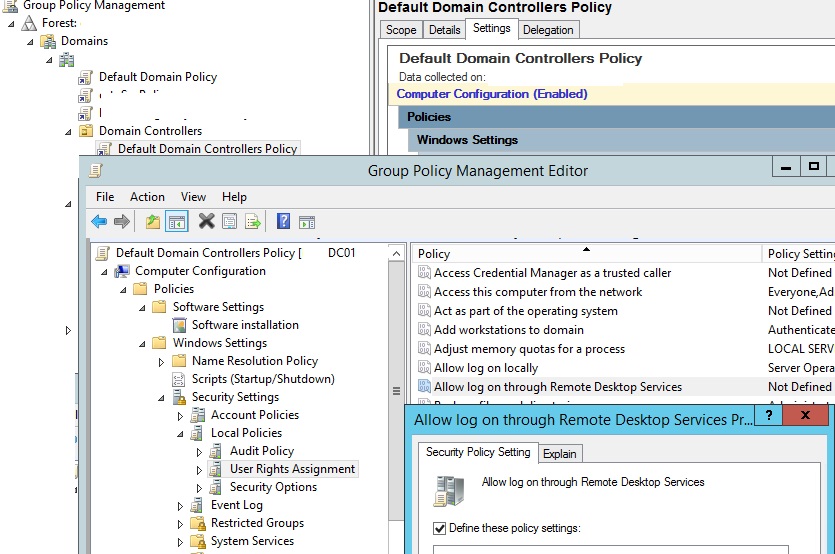
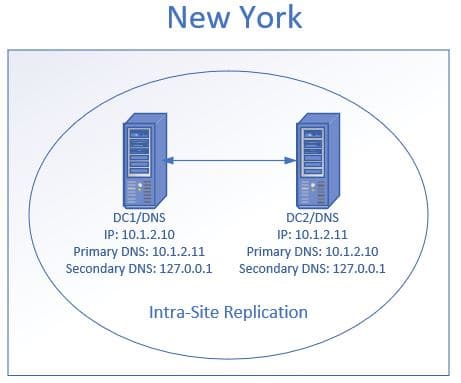
Do not use anything else between your clients and domain controller s. The first record in the file is the domain controller s lightweight directory access protocol ldap srv record. We can verify the query logging is working in our lab by simple making a dns request from a workstation we will see the query in the event view under the analytical log like below. Suspicious dns query signatures are looking for dns resolution to domains potentially associated with c2 traffic which could be an indication of a breached machine.
This will display the analytical log right click on this and select properties enable logging and do not overwrite events. What are suspicious dns query signatures. The value for preferred dns server remained the same the ip address of the windows server 2003 but as alternate dns server was set the loopback ip address of the newly promoted domain controller windows server 2012 r2 i e.