Domain Controller Post Exploitation

They have been seen doing this via group policies setting a startup item in the sysvol share or most commonly in recent attacks via psexec sessions emanating from the domain controller itself.
Domain controller post exploitation. Post exploitation part 4 setting up a domain controller. For the remainder of the screens click next. Dans l écran vérification de la configuration requise cliquez sur installer. This lesson covers using the smbexact command to set up a domain controller.
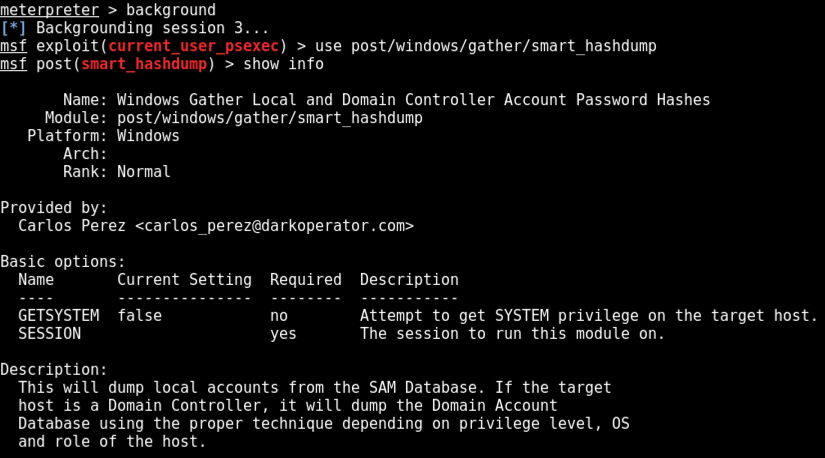
Participants learn how to obtain hashes from the domain controller which can be used to. The ryuk operators use stolen domain admin credentials often from an interactive logon session on a domain controller to distribute the ryuk payload. To simulate the attack to the domain we can setup an active directory virtual laboratory environment with a windows server 2012 r2 acting as domain controller. Mimikatz is a very popular and powerful post exploitation tool mainly used for dumping user credentials inside of a active directory network we ll be focusing on dumping the ntlm hashes with mimikatz and then cracking those hashes using hashcat i have already taken the time to put mimikatz on the machine dump hashes w mimikatz.
This can be good for finding other networks and. For the purposes of this post let s assume i ve landed on one of boxes in the network perhaps through a phishing attack or by just guessing bad credentials. On the prerequisite check screen click install. Sur les contrôleurs de domaine que vous prévoyez de mettre à niveau assurez vous que le lecteur qui héberge la base de données active directory ntds dit dispose d une quantité d espace disque disponible qui représente au moins 20 du fichier ntds dit avant de lancer la mise à niveau du système d exploitation.
Prints the list of domain controllers for the current domain. Net session find arp a. Udp port 88 for kerberos authentication udp and tcp port 135 for domain controllers to. Please tell me the required ports to communicate with domain controller mean to login a user to domain or join a machine to domain do i must required the rpc randomly allocated high tcp ports 1024 65535 hi below are the commonly required ports.
Post exploitation from the previous. Another important aspect about the domain controller security is that while passwords for local users are stored inside the machine they have been defined in passwords for domain users are stored on the dc itself. This time i was a little better in my it admin duties and had my domain controller and the rest of the network for my mythical acme company up and running after only one espresso. A lot of stuff has already been mentioned at obtaining windows passwords and dumping windows credential and bernardo blog dump windows password hashes efficiently part1 part2.
Domain active directory database domain controllers only credential manager credman store or lsa secrets in the registry and get all the passwords clear text or hashed. Net group domain controllers domain. Prints the machine s routing table. Participants learn step by step instructions on how to access admin passwords in a system and then create a new domain admin.
Lists all the systems currently in the machine s arp table. On domain controllers that you plan to upgrade make sure that the drive that hosts the active directory database ntds dit has free disk space that represents at least 20.