Domain Generation Algorithm Attack
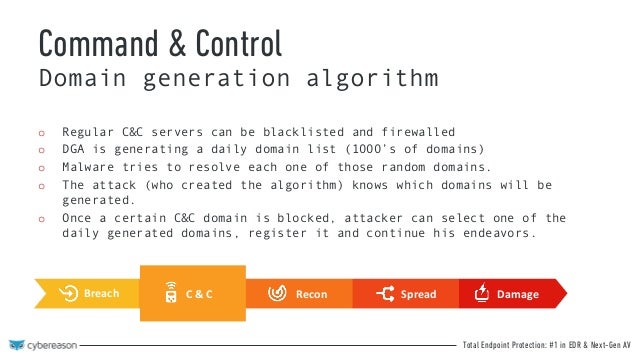
Domain generation algorithms dga are algorithms seen in various families of malware that are used to periodically generate a large number of domain names that can be used as rendezvous points with their command and control servers the large number of potential rendezvous points makes it difficult for law enforcement to effectively shut down botnets since infected computers will attempt to.
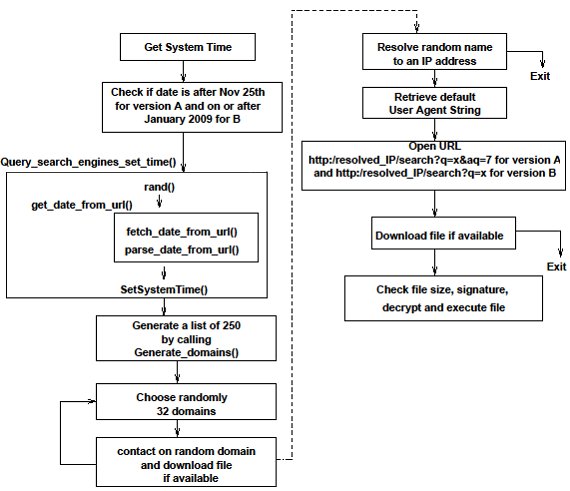
Domain generation algorithm attack. New targeted attack in the middle east by apt34 a suspected iranian threat group using cve 2017 11882 exploit. A domain generation algorithm is a program that is designed to generate domain names in a particular fashion. All dgas are based off of a static and dynamic seed which ensures that the domains are constantly changing. Figure 9 shows example network communications between a powruner backdoor.
Over the last decade domain generation algorithms dgas have become a popular tool for threat actors to deliver malware as it has become a difficult technique for defenders to counter attacks. Introduction 2020 is predicted to be an exciting year with more organizations adopting kubernetes than ever before. Retrieved december 20. Part of this is due to how the algorithm is set up and how easy they are to update.
Domain generation algorithm domain generation algorithms dgas can be used by malware to dynamically generate a set of candidate domains periodically to reach the c c center. Adversaries may make use of domain generation algorithms dgas to dynamically identify a destination domain for command and control traffic rather than relying on a list of static ip addresses or domains. As critical workloads with sensitive data migrate to the cloud we can expect to encounter various advanced persistent threats apt targeting that environment. There are many algorithms that are used to generate domains but many of these algorithms are simplistic and are very easy to detect using classical machine learning techniques.
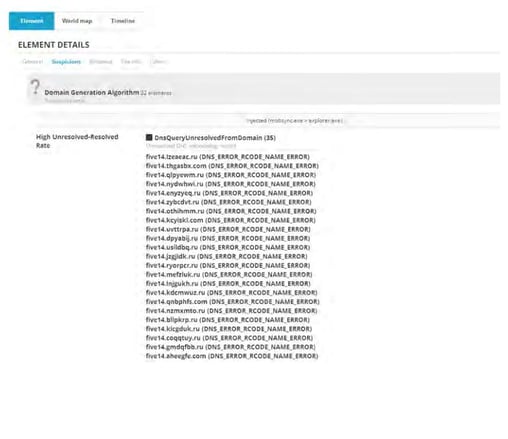
Domain generation algorithms create a constantly moving target that cyber defenders struggle to successfully hit with a blocklist. These domains are often used as rendezvous points for the servers that malware has command and control over. Some examples of the generated subdomains observed at time of execution include. Attackers developed dgas so that malware can quickly generate a list of domains that it can use for the sites that give it instructions and receive information from the malware usually referred to as command and control or c2.
Adversaries may use domain generation algorithms dgas to procedurally generate domain names for command and control communication and other uses such as malicious application distribution. As these dgas become more sophisticated and increasingly difficult to detect zvelo s cyber threat intelligence team is recommending heightened awareness as they anticipate this to be a prominent. Domain generation algorithm dga what is it. The botnet operator likewise uses the dga to calculate a domain name which they can register such that the dga domain is resolvable at the time when the bots attempt to.