Domain Generation Algorithm Decoder

Ipv6 literal external online tool to convert ipv6 address to corresponding literal address.
Domain generation algorithm decoder. Please cite the following papers if you use the code as part of your research. Domain generation algorithms dgas are frequently used to generate large numbers of domains for use by botnets. Domain generation algorithms create a constantly moving target that cyber defenders struggle to successfully hit with a blocklist. Using a domain generation algorithm dga based on the current time or some other information publicly available across all hosts each only valid for a short amount of time.
Depending on the selected function the initialization vector iv field is. Reverse ip use reverse ip lookup rdns arpa domain and ptr record and dns resolution to determine domain name by ip address. There are many algorithms that are used to generate domains but many of these algorithms are simplistic and are very easy to detect using classical machine learning techniques. This week i am going to talk about catching its injected entry point inside explorer exe.
Infected hosts lookup all candidate values. Later that year conficker made dga a lot more famous. Using the input type selection choose the type of input a text string or a file. Then select the cryptographic function you want to use in the function field.
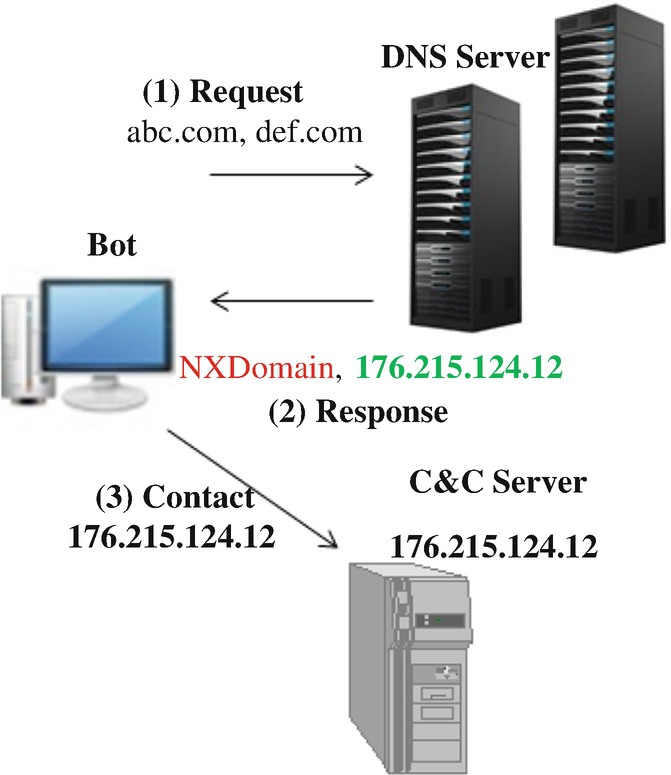
These domains are often used as rendezvous points for the servers that malware has command and control over. Kraken was the first malware family to use a dga in 2008 that we could find. Domain generation algorithms dga are algorithms seen in various families of malware that are used to periodically generate a large number of domain names that can be used as rendezvous points with their command and control servers the large number of potential rendezvous points makes it difficult for law enforcement to effectively shut down botnets since infected computers will attempt to. A domain generating algorithm dga is a program or subroutine that provides malware with new domains on demand or on the fly.
Decoding domain generation algorithms dgas part ii catching zeusbot injection into explorer exe last week i talked about unpacking this binary for static analysis. Part i decoding domain generation algorithms dgas part ii catching zeusbot injection into explorer exe at this point you can go ahead and close the two parent processes since we are not interested in their functionality for the sake of simply finding the dga. Also ip ipv6 calculator shows longest and shortest ipv6 versions variations. In addition to the short validity dgas frequently generate also hundreds of candidate do mains per time interval.
Part of this is due to how the algorithm is set up and how easy they are to update. All dgas are based off of a static and dynamic seed which ensures that the domains are constantly changing. Evaluating deep learning approaches to characterize and classify the dgas at scale journal of intelligent and fuzzy systems ios press detecting malicious domain names using deep learning approaches at scale.