Domain Generic Dns Response Notimp Exploit

A trace outputs the following.
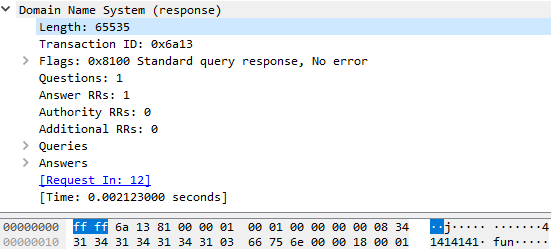
Domain generic dns response notimp exploit. 20090320 19 44 52 f00 packet udp rcv 124 124 54 15 f3a2 u 0028 noerror 9 mydomain 3 com 0 udp question info at 007fe460 socket 444 remote addr 124 124 54 15 port 53098 time query 51164 queued 0 expire 0. It looks like you re only replying to a queries from your dns server which might explain why some nameservers don t like your domain. Between 6 pm and 9 pm in dublin 20 of the queries from european clients receive the ip address of the web server in the seattle datacenter in their dns query response. Bind 9 4 1 9 4 2 remote dns cache poisoning metasploit.
A servfail answer tells you there s an issue reaching the dns server for your domain or that it isn t set up properly. The next method of enumeration is the reverse lookup a typical dns query where a name is resolved to an ip is known ad a forward lookup a reverse is just the opposite where we query is made for an ip and we get the fqdn fully qualified domain name for the ip this method of enumeration tends to go un noticed by administrators and ips ids. A dns exploit is a vulnerability in the domain name system dns through which an attacker an infiltrate a network. A 2016 infoblox security assessment report analyzing 559 files of captured dns traffic found that 66 percent of the files showed evidence of suspicious dns exploits.
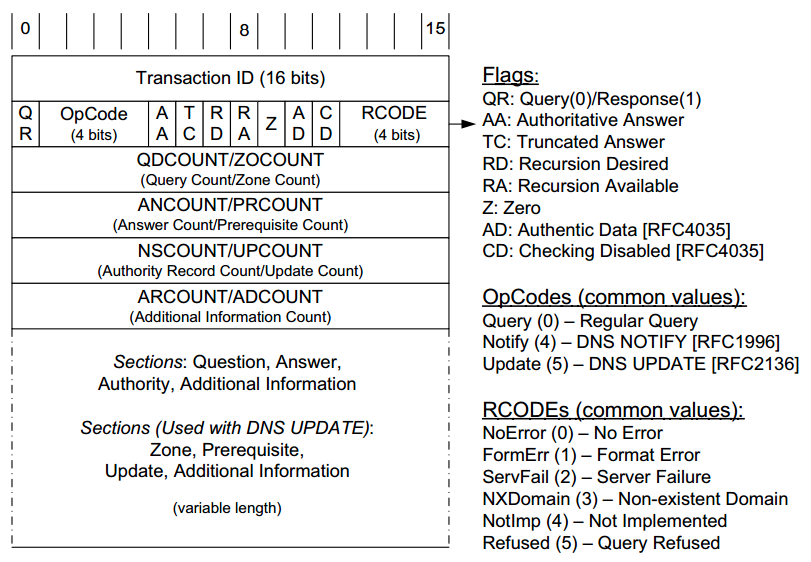
Classes in the range 32768 to 65535 are incompatible with multicast dns. Remote exploit for windows platform. Dns classes expert s unassigned reference note as noted in multicast dns can only carry dns records with classes in the range 0 32767. Update notify a sub domain into our domain and the ms dns server rejected this attempt with a notimp response.
Between 6 pm and 9 pm in seattle 20 of the queries from. Remote exploit for multiple platform. This attack works by sending random hostname queries to the target dns server coupled with spoofed replies to those queries from the authoritative nameservers for that domain. Microsoft dns server dynamic dns update change.
Dig 9 8 2rc1 redhat 9 8 2 0 23 rc1 el6 5 1 trace iwanhae ga. American dns clients receive the ip address of the web server in the seattle datacenter in their dns query response.