What Is Domain Hijacking And Malicious Transfer

To perform the attack perpetrators either install malware on user computers take over routers or intercept or hack dns communication.
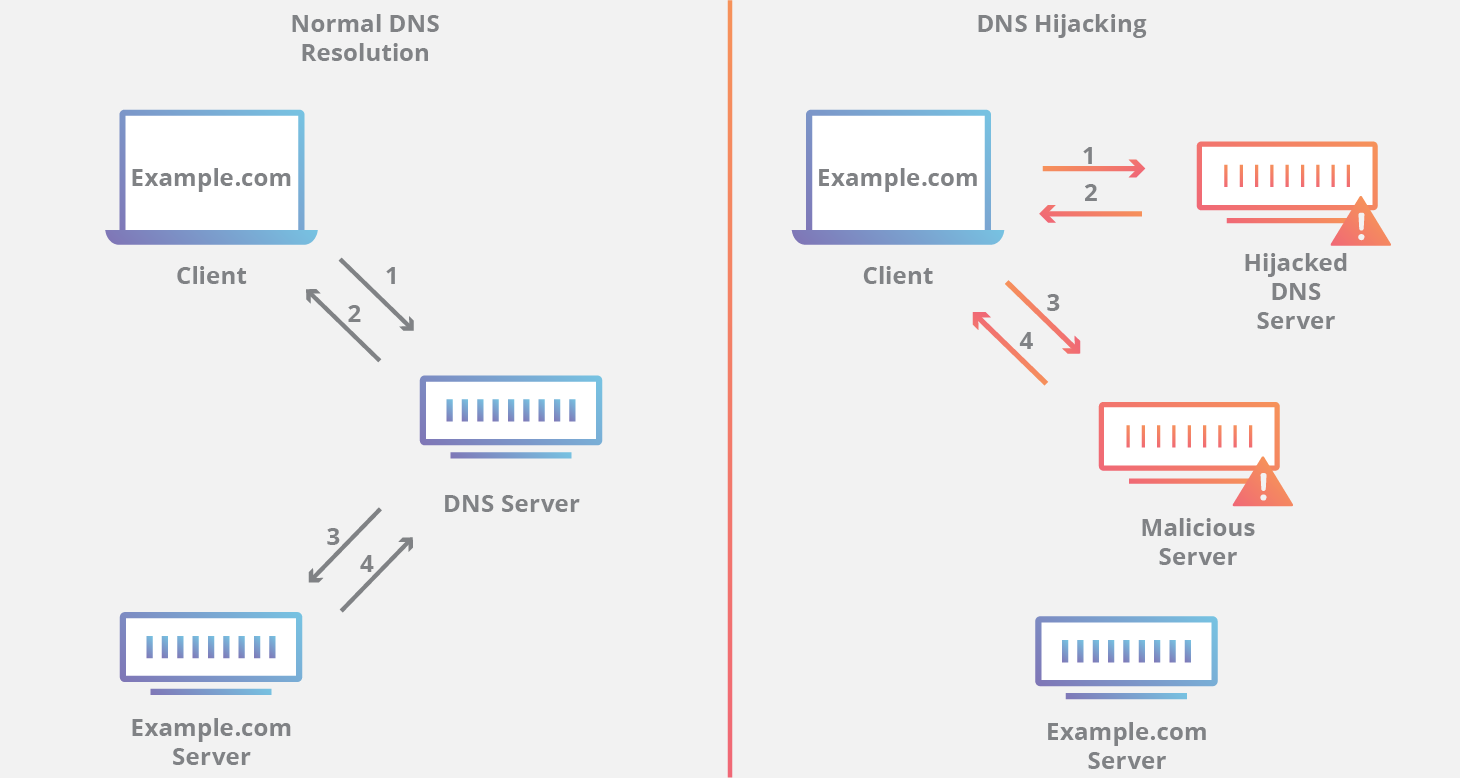
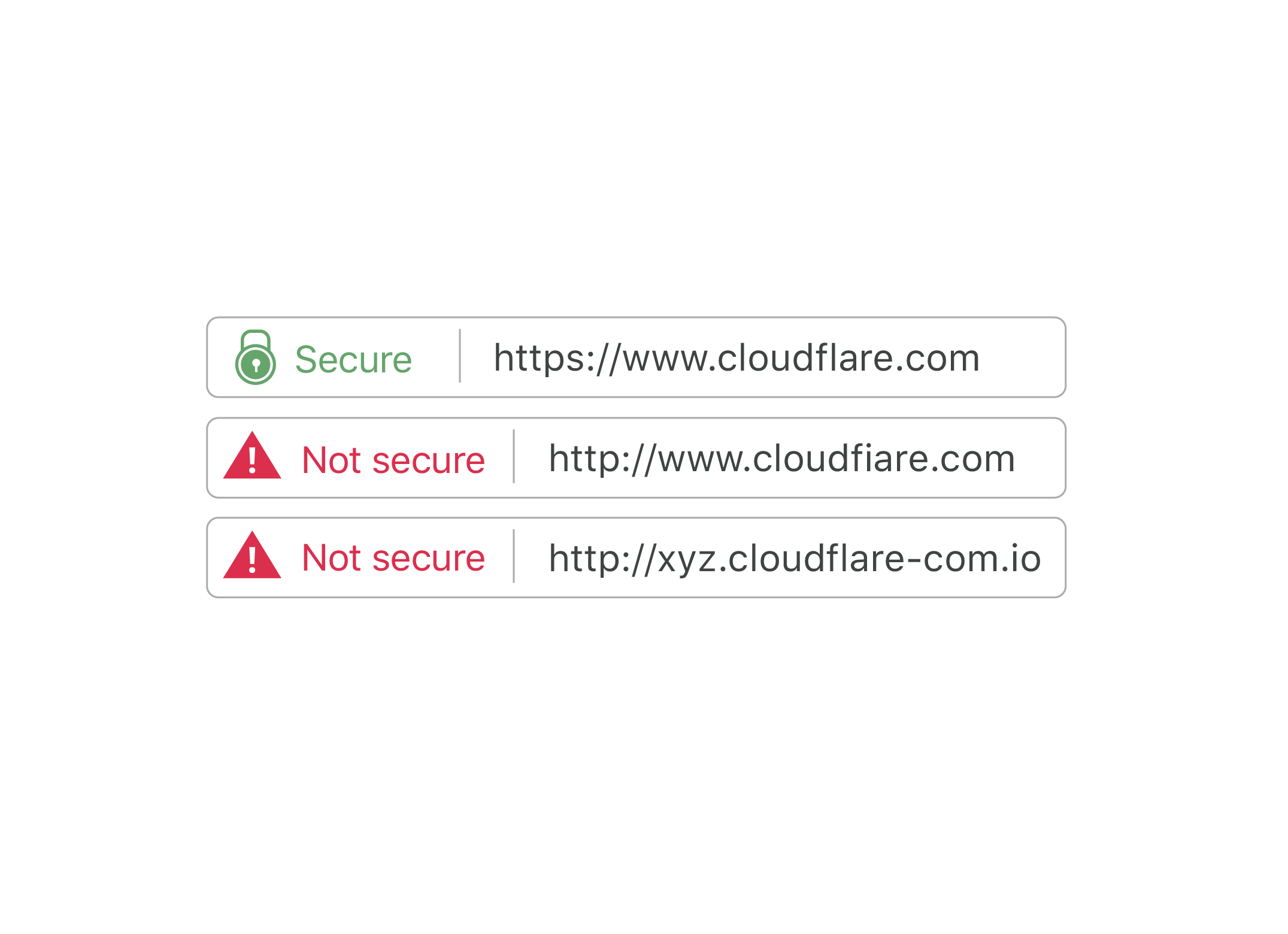
What is domain hijacking and malicious transfer. Dns hijacking manipulates the transaction and makes users unaware of the servers that they are using during an internet session. Hijacking can happen due to security flaws on your end or the end of your domain hosting company. Domain hijacking is broadly defined as an attempt to transfer ownership or control of a domain from its rightful owner. Means when an attacker takes control of a computer to alter it s dns settings so that it now redirect to a rogue dns server the process is called as dns hijacking.
This sort of activity often harms the legitimate domain owner. Often a hijacker s motivation isn t monetary gain but rather purely for the challenge for malicious intent or for hacktivism. The rightful owner loses control of the domain name in the process. Domain hijacking often involves a fraudulent registrar transfer request or otherwise false change the registration of a domain.
Impersonating domain name owner to persuade domain registrars to amend information or transfer domain names to other. Are common ways hackers use to hijack domain names. Domain hijacking is a form of theft where the attacker takes access to a domain name without the consent of the original registrant. Once a hacker has accessed their targets domain control panels a common tactic is to transfer the domain name to redirect internet traffic through external hosts.
A hacker tries to get access to his target s complete domain registrar account details that will allow him to make unauthorized changes and transfers to his advantage. The term domain hijacking domain name hijacking domain theft applies to a situation when a malicious party actually takes over the control of a domain name. Domain hijacking or domain theft is the act of changing the registration of a domain name without the permission of its original registrant or by abuse of privileges on domain hosting and registrar software systems. This process however is the reason why domain hijacking is possible.
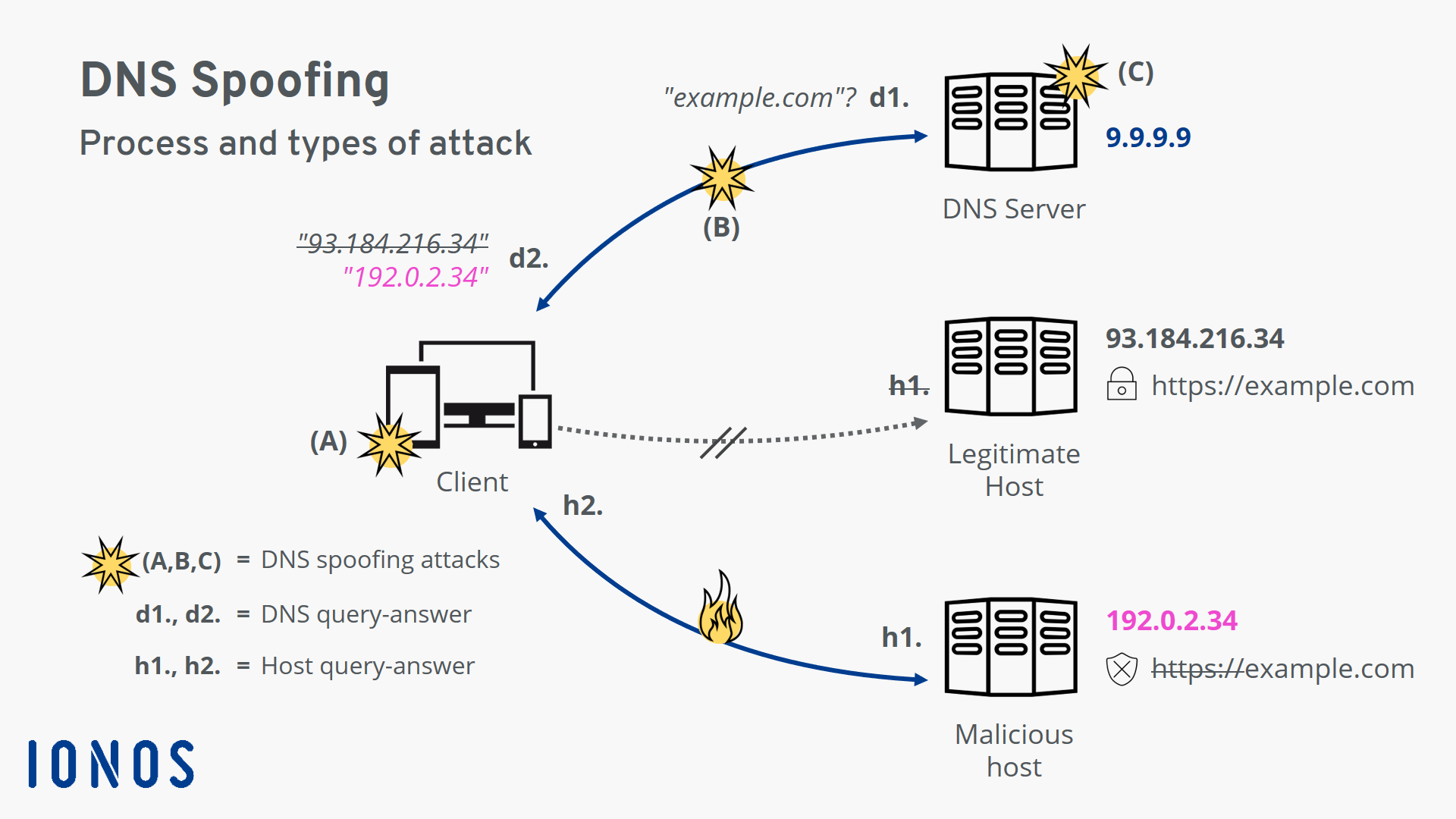
How is it done. Dns hijacking is a type of malicious attack that creat dns redirection of computer s tcp ip settings to point it at a rogue dns server. This can be. This can be devastating to the original domain name holder not only financially as they may have derived commercial income from a website hosted at the domain or conducted.
What is domain hijacking. Domain name server dns hijacking also named dns redirection is a type of dns attack in which dns queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites. Domain name hijacking is just a fancier way to say that your domain name has been stolen.