Domain Controller Event Logs

Account logon events are generated on domain controllers for domain account activity and on local devices for local account activity.
Domain controller event logs. However for expediency sake the service account for this was added to the domain admins group and now we re trying to get it out of there. Interactive logon this is used for a logon at the console of a computer. Bad passwords and time synchronization problems trigger 4771 and other authentication failures such as account expiration trigger a 4768. These events occur on domain controllers when users or computers log on to the ad domain so yes collecting the domain controllers is what you want to do.
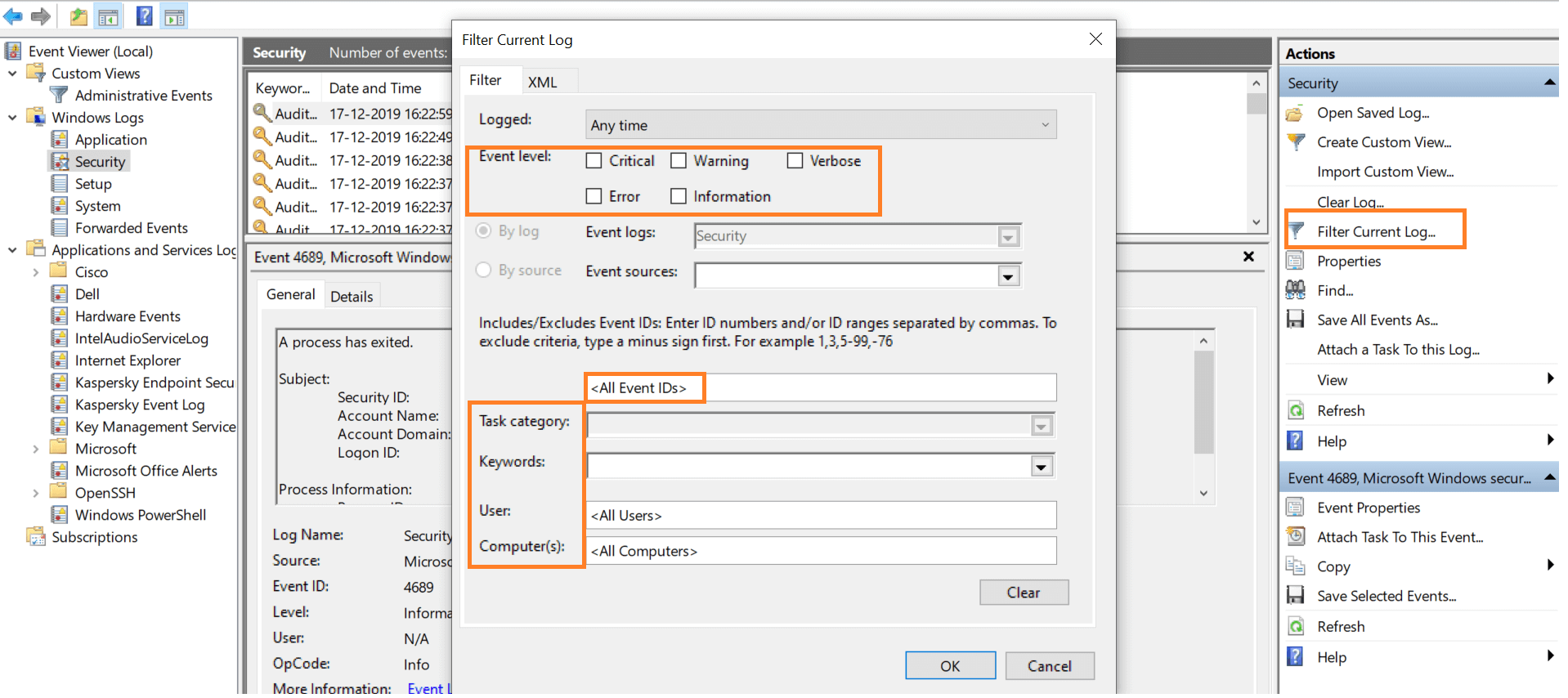
Well let me tell you it s easier said than done. Built in logs for troubleshooting. The result code in either event specifies the reason for why authentication failed. In the options menu select set date range.
Again it is worth mentioning to say it all depends on the environment and you can start to query audits right after or wait a couple of days to get populated. In the event ids box type a space and then type 12294 after the last event number. A type 2 logon is logged when you attempt to log on at a windows computer s local keyboard and screen. If the user fails authentication the domain controllers logs event id 4771 or an audit failure instance 4768.
All of these logs are enabled and configured for maximum verbosity by default. Basically the rule of thumb for this setting is if you like to have logon audits of 10 days before you have to wait about 10 days after increasing the. There was no way i was going to logon to dozens of. The problem is if you have more than one domain controller you should the record that you need can be on any of them.
If both account logon and logon audit policy categories are enabled logons that use a domain account generate a logon or logoff event on the workstation or server and they generate an account logon event on the domain controller. All domain controllers for the domain appear in the select to search right click to add box. If you do not have access to the adrap tool and want to check event logs on all the domain controllers you can use a powershell script that we will be explaining in this. As long as you have audit logging enabled the data you are after is in the event logs of your domain controllers.
The built in logs are the most important instrument for troubleshooting issues with domain controller promotion and demotion. Client computer collector log on to your client computer windows vista and above with an account which is member of the domain admins group. Built in logs for troubleshooting. Therefore your client computer is the collector und your domain controller is the target.
Also in the event ids box you see that event ids 529 644 675 676 and 681 are added. Network logon this logon occurs when you. At my day job we have quite a few dcs and i needed to know which admin created a particular ad account. One of the accounts that was there was for our siem to get at domain controller security event logs somewhat important to keep and log and monitor.
When a user logs on at a workstation with their domain account the workstation contacts domain controller via kerberos and requests a ticket granting ticket tgt. Additionally interactive logons to a member server or workstation that use a domain account generate a logon event on the domain.



.jpeg)