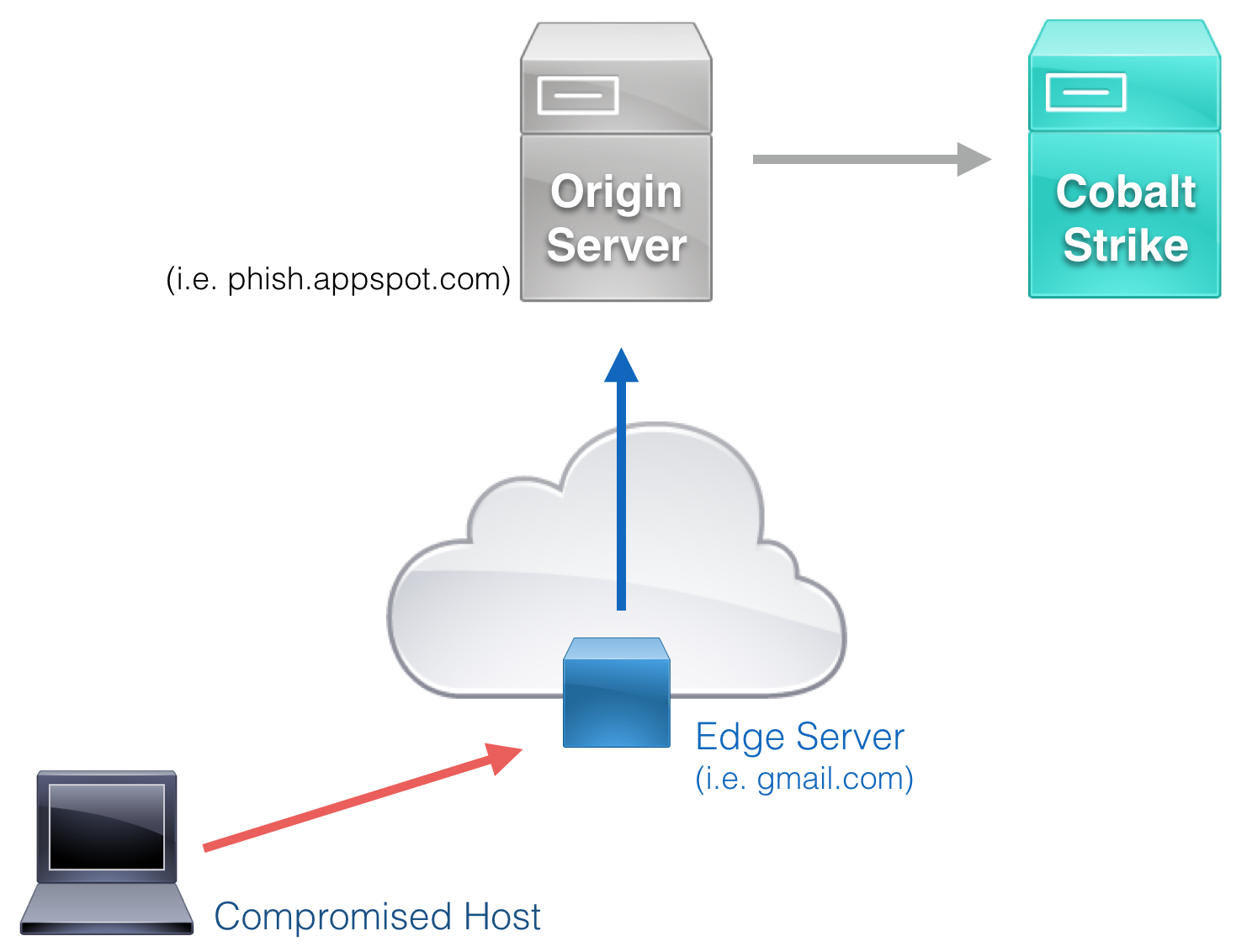
Domain Fronting Palo Alto
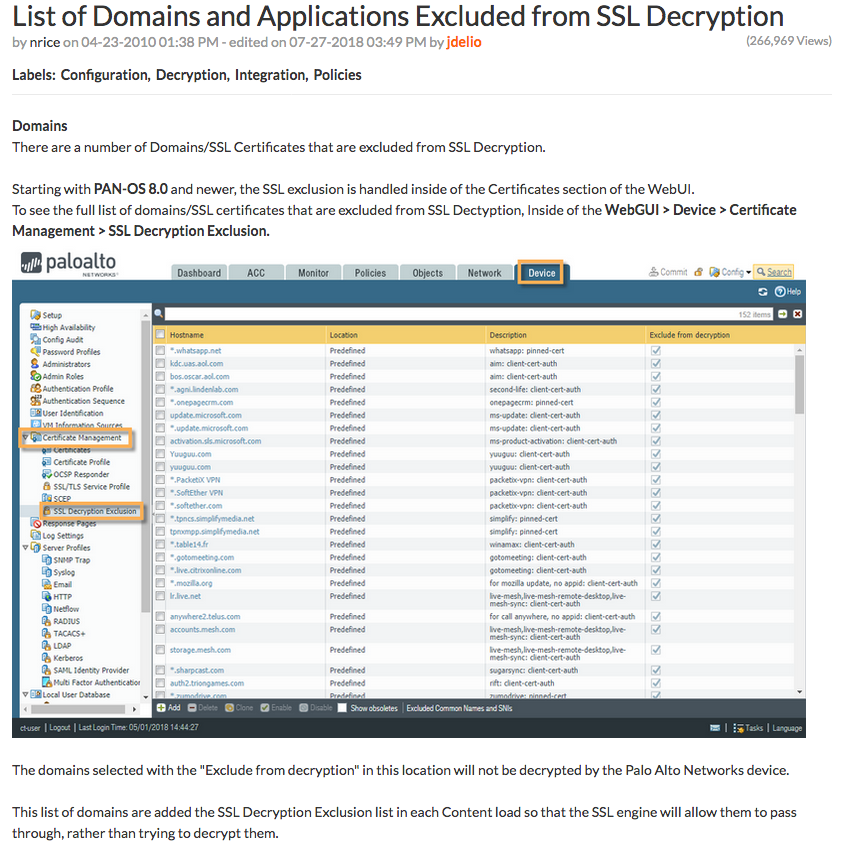
If palo alto networks is configured to alert on young domains rather than block it may be that you are correlating with other log sources to perform broader analytics that results in an ai engine alert indicating a malicious young domain with a high degree of certainty.
Domain fronting palo alto. Create a custom url category by going to objects custom objects url category. Palo alto networks fixes critical flaw in pan os firewall software. When you configure a split tunnel to include traffic based on the application process name or destination domain and port optional all traffic for that specific application or domain is sent through the vpn tunnel for inspection and policy enforcement. Split tunnel traffic is not inspected by next generation firewall and therefore does not have the threat protection offered by palo alto networks.
These windows 10 tools give you complete control over privacy. In order to block a list of url s globally create a custom url category and add url s to the category and then place that into a rule. Us staffing firm artech discloses ransomware attack data breach. Pa extracts the host header so in theory it should be possible 253882.
Hi did anyone manage to write a custom signature to detect domain fronting. Redirect to a different domain based on url filtering objective. Palo alto networks next generation security platform enables domain to proactively guard against cyberthreats without slowing down end user productivity. Why and how individuals and enterprises need to pay registrars icann accredited domain resellers an annual fee to buy domain names and become domain owners.
In this case you may wish to proactively block that domain on the palo alto networks device. Palo alto networks next generation firewall customers can block the parked category with the url filtering and dns security subscriptions. You wish to redirect specific website domain to a different domain. Moreover domain maintains continuous prevention against known and unknown threats with minimal staff overhead thanks to a comprehensive threat intelligence dashboard.