Domain Generation Algorithm Example

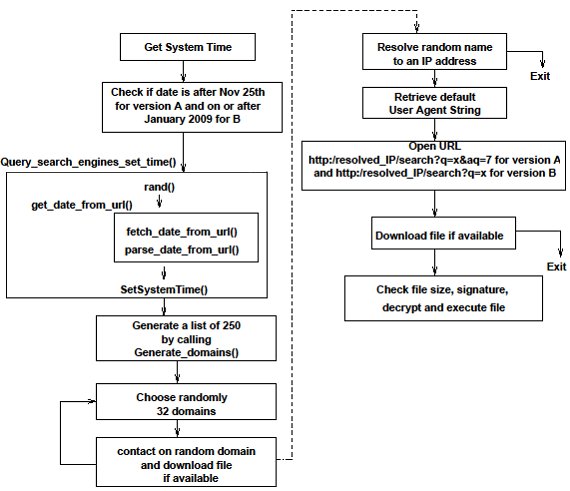
A malware that uses a domain generation algorithm can generate thousands of domain names at once.
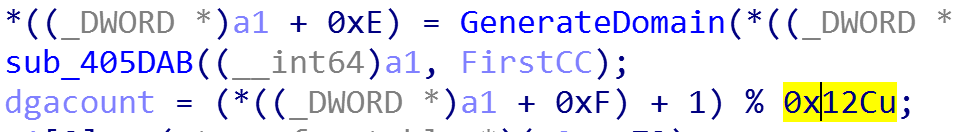
Domain generation algorithm example. Cybereason published an excellent article a bazar of tricks. Dissecting domain generation algorithms. The domain generation algorithm has remained a main source of communication for malware in the past 10 years.
There are many algorithms that are used to generate domains but many of these algorithms are simplistic and are very easy to detect using classical machine learning techniques. Dgas are designed to generate quick random seeds such as dictionary words dword values random digits gibberish strings hcbhjbdjbjhsb ru as domains which can be used to provide instructions for malware to exfiltrate data provide. Domain generation algorithms dga are algorithms seen in various families of malware that are used to periodically generate a large number of domain names that can be used as rendezvous points with their command and control servers the large number of potential rendezvous points makes it difficult for law enforcement to effectively shut down botnets since infected computers will attempt to. For more technical details we can recommend.
Conficker c for example can generate up to 50 000 domain names per day and only 500 of these are queried. Domain generation algorithm dga what is it. Over the last decade domain generation algorithms dgas have become a popular tool for threat actors to deliver malware as it has become a difficult technique for defenders to counter attacks. Therefore threat actors would need to register a portion of these dga generated domain names.
Due to the fact that dga domains are generated randomly they tend to be. Dga is a technique that fuels malware. As these dgas become more sophisticated and increasingly difficult to detect zvelo s cyber threat intelligence team is recommending heightened awareness as they anticipate this to be a prominent. The idea is that two machines using the same algorithm will contact the same domain at a given time so they will be able to exchange information or fetch instructions.
Following team9 s development cycles they only show the seeding part of the domain generation algorithm however the listing of generated bazar domains matches the algorithm in this blog post apart from the first two domains alztwfdicu bazar and ocgjqlaspr bazar which are hardcoded. Domain generation algorithms dgas are frequently used to generate large numbers of domains for use by botnets. Domain generation algorithm dga represents a safe haven for modern botnets as it enables them to escape detection. Domain generation algorithm monitoring.
An analysis to discover the dga.