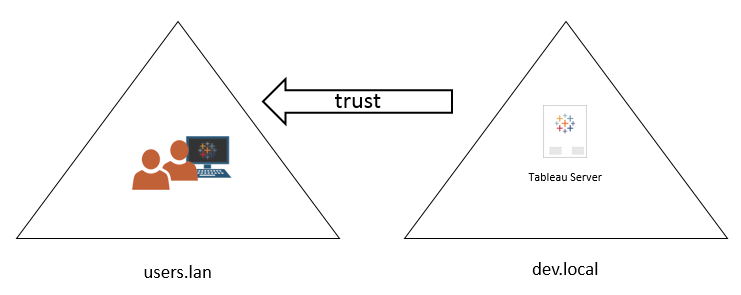
Domain Trust Group Policy

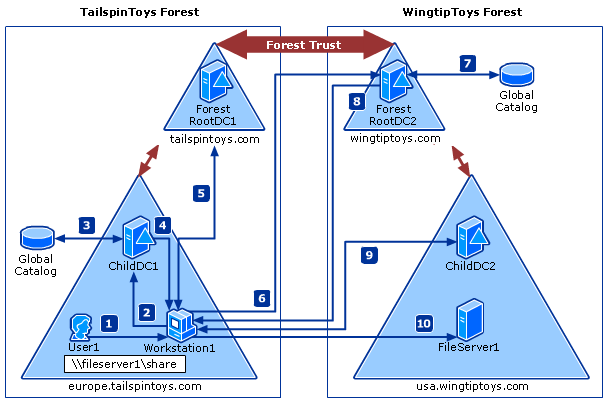
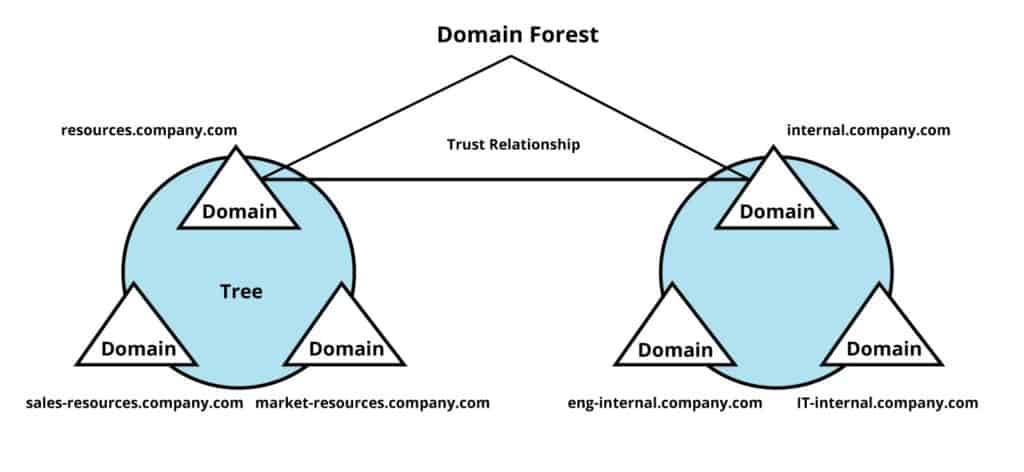
However you must have trust between the domain you want to add and the domain of your user object.
Domain trust group policy. Every windows os comes with a native firewall as the basic protection against malicious programs windows firewall controls the incoming and outgoing traffic from and to the local system based on the criteria defined in the rules. In a domain environment administrator can centrally configure windows firewall rule using group policy. The criteria can be program name protocol port or ip address. My issue is relating to group policy.
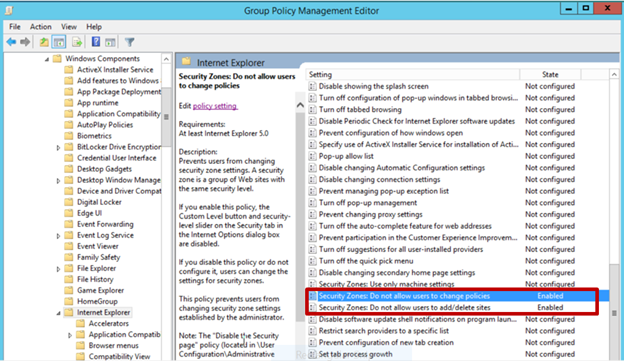
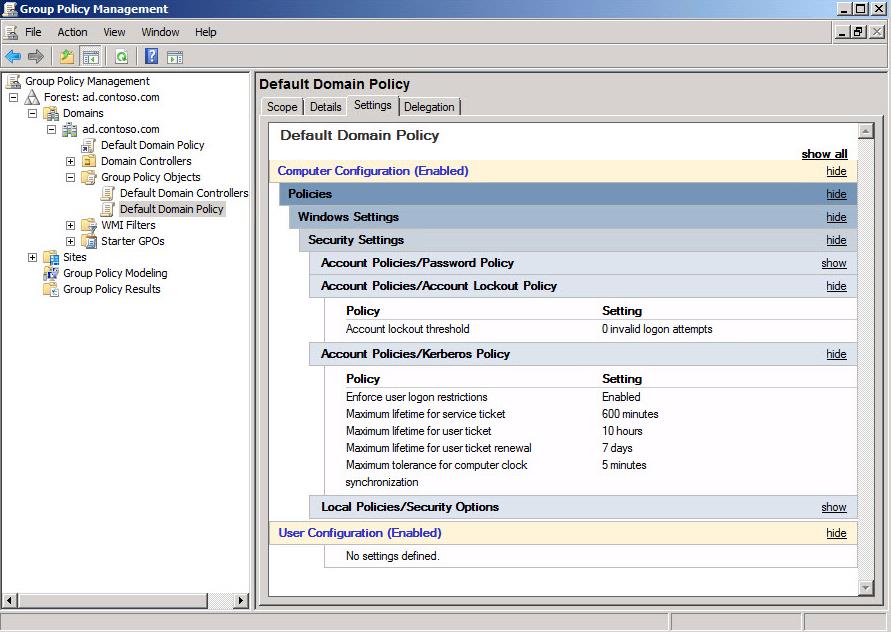
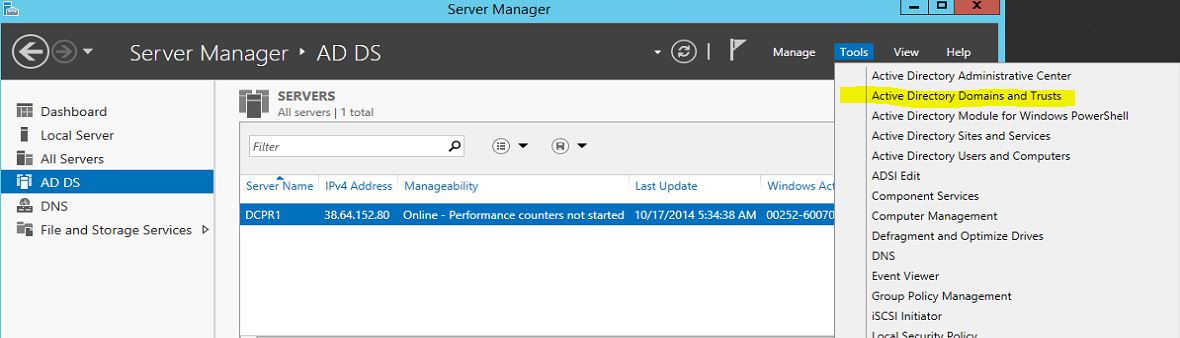
In the left pane navigate to computer configuration administrative templates windows components internet explorer internet control panel security page double click on site to zone assignment list in the right pane. Press windows r key combination to invoke run dialog input gpedit msc to the box and click on ok. I would think logically global or universal should be required to span a trust and local should be excluded but it is completely opposite for whatever reason. In the group policy management console gpmc console tree right click group policy management and then click add forest.
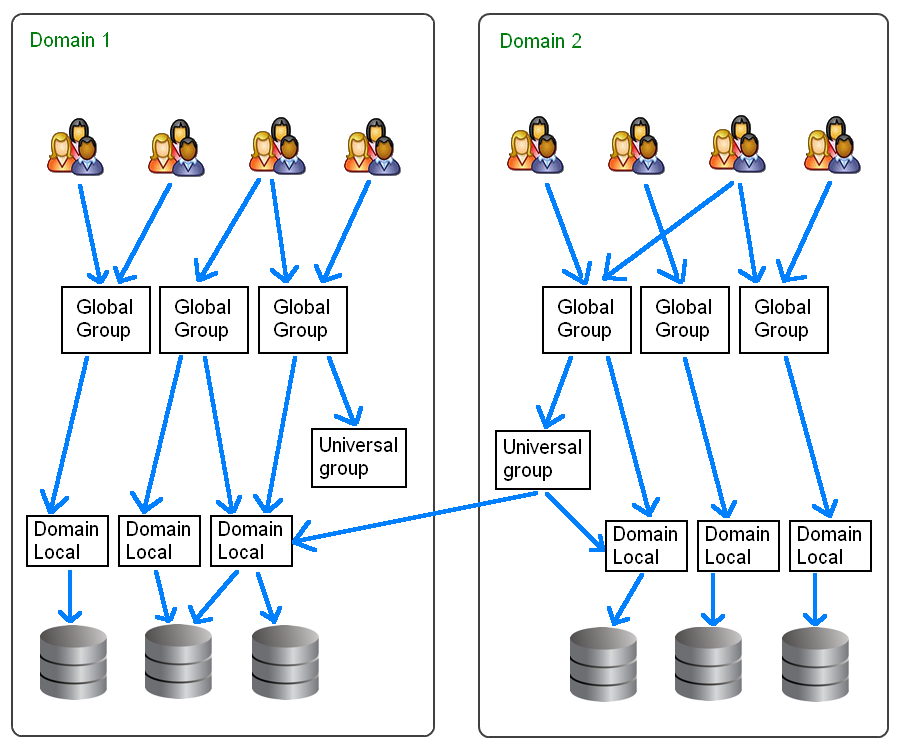
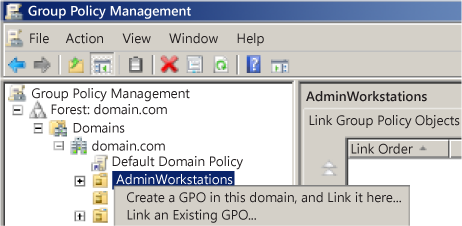
In the add forest dialog box type the dns or netbios name of any domain in the forest and then click ok. In order to be able to create a security group and add users from either domain trust the security group scope must be domain local. In the group policy management console right click and select create a gpo in this domain and link it here tip. For example an administrator can remove the use of run command from the start menu.
This will be a user based gpo so make sure you link the gpo to a location that will target the users. I have all of my users separated into an ou called adpro users i ll. So now there is a three way forest trust in effect and working fine for file access. How to add trusted site to group policy windows 10.
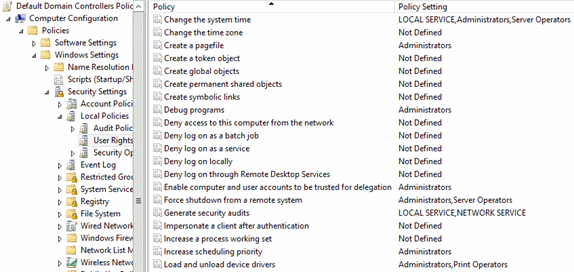
To add a forest. Open the group policy management console. The group policies are of two types local group policy and domain based group policy. This feels completely backwards to me though.