Cross Domain Data Hijacking Owasp
A8 2017 insecure deserialization a10.
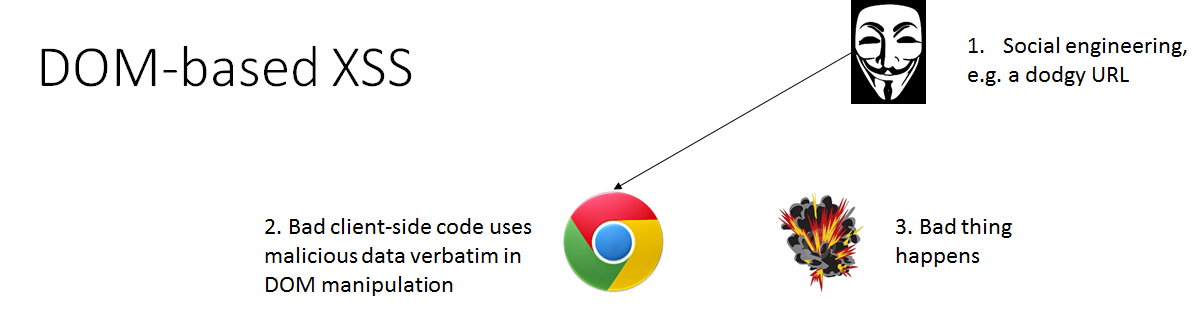
Cross domain data hijacking owasp. It s a security mechanism that doesn t permit to malicious domains to access to cookies and tokens of the attacked domain for making http request cross domain. The same origin policy is a restrictive cross origin specification that limits the ability for a website to interact with resources outside of the source domain. Apart from the above two scenarios when one website reads data from another website it is called as cross origin resource sharing aka cors. In cross site scripting or xss attackers can include malicious code in a legitimate web application and when a victim visits the app it will execute the injected code and deliver the malicious script to the user s browser and hijack user sessions redirect users to malicious sites and damage the targeted website.
This page is possibly vulnerable to cross domain data hijacking. This is why we believe that cross site scripting will make a comeback in the 2021 edition of owasp top 10 with a predicted a3 2021 classification. Released under agpl see license for more information. Exploiting websites with insecure policy files crossdomain xml or clientaccesspolicy xml by reading their contents.
Interact with files of the victim s website by using current user s cookies execute javascript communicate with its source domain without checking the cross domain policy use the flash file to send requests and to read files from the domain of 9. Web browser data loading may be possible due to a cross origin resource sharing cors misconfiguration on the web server. The same origin policy was defined many years ago in response to potentially malicious cross domain interactions such as one website stealing private data from another. To prevent any cross domain data leakage etc.
Cors is a w3 specification that allows cross domain communications from the browser. With javascript it doesn t allow javascript from domain a to access content data from domain b in the case of xhr the same origin policy does not allow for any cross domain xhr requests. Passive scan rule description. This project can be used to provide a proof of concept for.
The same origin policy controls interactions between two different origins isolating malicious domains to access resources and data cookie token of other domains. This relatively new type of vulnerability can still. Cross site content data hijacking xsch poc project license. It works by adding new http headers that describe the origins that are allowed cross domain information sharing.